This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
The Ultimate Guide to Fake Emails: Understanding, Identifying, and Protecting Yourself
Written by
NetizensJuly 5, 2024
10 min read

Your bank sends you an urgent email when you open your inbox, alerting you that your account has been locked unless you immediately confirm your information. After entering your password and clicking the link, you realize your mistake. You just gave a scammer your login credentials. Phishing attacks, in particular, are more sophisticated, cunning, and dangerous than ever in 2026. Because phishing accounts for 92% of data breaches and over 320 billion emails are sent every day, cybercriminals are profiting from our trust. This comprehensive guide explores the definition of bogus emails, how to identify them, and how to stay safe in the world of AI-powered scams.
What Are Fake Emails?
Fake emails are deceptive messages that pretend to come from trusted sources, like your bank, Amazon, or even a colleague, to trick you into harmful actions. They’re the digital equivalent of a wolf in sheep’s clothing, often using spoofed sender addresses to appear legitimate.For example, an email from “[email protected]” (note the “1” instead of “l”) might look real at a glance. Similar scams like the Geek Squad scam email show how attackers impersonate trusted brands to trick users into giving away personal or financial information.
Their objectives? Install malware, steal your passwords, or con you out of money. With perfect grammar and customized information taken from social media or data breaches, these emails look eerily realistic in 2026 thanks to AI tools like generative text models. Fake emails are malicious, costing victims billions of dollars every year, $50 billion worldwide in 2025 alone, according to FBI reports—in contrast to spam, which is annoying but usually harmless.
Types of Fake Emails
There are many different types of fake emails, and each has its own strategies. Based on the most recent cybersecurity data, here is a summary of the most prevalent types in 2026:
| Type | Description | Common Tactics | Example Targets |
|---|---|---|---|
| Phishing | Broad attacks impersonating trusted entities to steal credentials or data. | Links to fake login pages; requests for verification. | Banks, social media (e.g., fake Facebook login). |
| Spear Phishing | Targeted phishing using personal details for credibility. | Customized messages referencing recent activity. | Executives or specific employees (e.g., CEO fraud). |
| Business Email Compromise (BEC) | Fraudulent emails targeting businesses for wire transfers or data. | Spoofed executive requests for payments. | Finance teams; losses exceed $2.7B annually. |
| Vishing/Smishing | Voice (phone) or SMS phishing, often starting with email prompts. | Calls/texts urging clicks on email links. | Delivery services (e.g., fake UPS package alerts). |
| Malware Attachments | Emails with infected files disguised as invoices or updates. | Attachments like “Invoice.pdf.exe” that install ransomware. | HR or accounting departments. |
| Brand Spoofing | Imitates popular brands with near-identical logos and layouts. | Fake Amazon order confirmations. | E-commerce users during sales seasons. |
| Quishing | QR code phishing embedded in emails or flyers. | Scans lead to malicious sites. | Public spaces or promotional emails. |
| Advance-Fee Scams | Promises rewards in exchange for upfront fees or info. | “Nigerian Prince” variants or fake lotteries. | Unsuspecting individuals via mass emails. |
With tools that create emails that imitate the writing styles of your contacts, artificial intelligence has accelerated these scams. Crushing at public events has increased, according to X posts from late 2025.
The Risks of Falling for Fake Emails
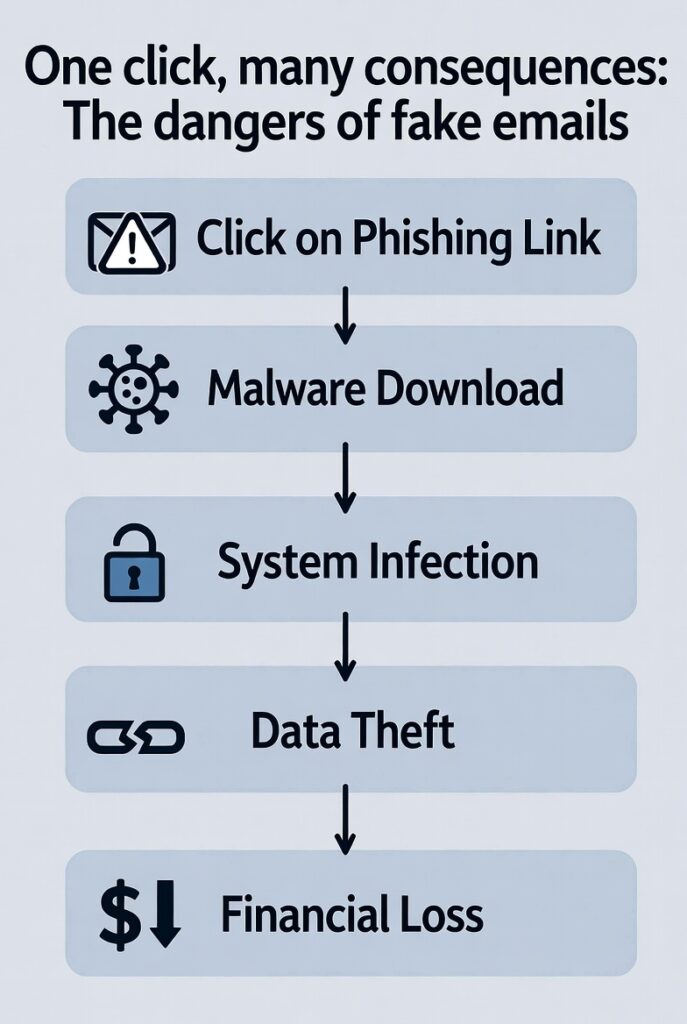
One wrong click can spiral into chaos. Here’s what’s at stake:
- Financial Loss: Scammers drain accounts or trick you into fraudulent payments. BEC scams alone cost businesses $3.2 billion in 2025.
- Identity Theft: Stolen data leads to fake accounts, ruined credit, or stolen tax refunds. Recovery can take years.
- Malware/Ransomware: Malicious links or attachments lock your device, demanding hefty ransoms (average: $2.5M for enterprises).
- Data Breaches: Compromised emails expose sensitive info, risking fines (e.g., GDPR penalties up to 4% of revenue).
- Reputational Harm: Businesses lose customer trust; individuals face job or social fallout.
A case from 2025: A small business lost $100,000 when a worker installed ransomware that rendered operations impossible after clicking on a phony invoice link. Although it’s safe to open an email without clicking, links and attachments can change everything.
How to Identify Fake Emails
Spotting fakes takes practice, but this 30-second checklist makes it easier:
1. Verify the Sender: Hover over the “From” field. Legit emails use official domains (e.g., @microsoft.com), not @micr0soft-support.net or Gmail.
2. Watch for Urgency: Phrases like “Your account expires in 24 hours!” scream scam. Real companies give clear timelines.
3. Check Links/Attachments: Hover over links to see the real URL. Avoid unsolicited files, use antivirus to scan if unsure.
4. Spot Errors: Typos, awkward phrasing, or generic greetings (e.g., “Dear Customer”) are clues. AI reduces this, but subtle errors persist.
5. Examine Design: Blurry logos or mismatched fonts? Suspicious. Legit emails are sleek and branded.
6. Confirm Directly: Don’t reply or click, visit the official site or call a verified number. And if you’ve accidentally sent a sensitive message, learn how to unsend an email in Outlook to quickly reduce your risk.
7. Use Tech: Gmail/Outlook’s AI filters flag fakes; enable 2FA and spam blockers.
In 2026, tools like Zero Trust email gateways and AI-driven phishing detectors (e.g., Barracuda Sentinel) are must-haves for businesses.
Real-World Examples
Let’s break down some 2026 phishing attempts (anonymized for safety):
- Fake PayPal Alert: Subject: “Your account is restricted!” Sender: [email protected]. Urges clicking a link to “restore access.”
Red Flag: Spoofed domain; no prior account issues. - HR Malware Scam: Attachment labeled “Payroll_Update_2026.pdf.exe” from a fake HR email. Installs spyware.
Red Flag: Unexpected file; double extension (.pdf.exe). - Tax Refund Fraud: “Claim your $750 refund!” from [email protected]. Links to a fake IRS portal.
Red Flag: Government never emails for refunds. - Quishing Scam: A “delivery update” email with a QR code to “track your package.” Scans lead to a credential-stealing site.
Red Flag: Unsolicited QR code.
X posts in 2026 report a rise in AI-crafted emails mimicking colleagues, complete with stolen email signatures.
Prevention and Response Strategies
Stay safe with these proactive steps:
- Enable Security: Use 2FA, antivirus with phishing detection (e.g., Norton 360), and email filters. DMARC/SPF for businesses. Choosing one of the best email providers with built-in spam and phishing protection can further reduce your exposure to fake emails.
- Train Yourself: Try free phishing quizzes on Phishing.org or KnowBe4 to sharpen your skills.
- Verify Sources: Manually type URLs or call official numbers. Never trust email links.
- Report Fakes: Forward to [email protected] or your email provider. Block suspicious domains.
If You Fall Victim:
- Change passwords immediately (use a password manager like LastPass).
- Monitor accounts for unusual activity.
- Freeze credit with Equifax/TransUnion.
- Report to the FTC (reportfraud.ftc.gov) or local authorities.
- Check breaches on Have I Been Pwned?.
Businesses: Train employees quarterly and use AI tools like Proofpoint for real-time threat detection.
The Future of Fake Emails in 2026 and Beyond
Fake emails are developing with AI in 2026. Using information from compromised databases or X profiles, scammers utilize generative AI to create perfect, highly customized messages. AI-generated QR codes and deepfake audio in vishing scams (triggered by emails) are on the rise. According to experts, 70% of phishing emails will use AI to perfectly imitate trusted contacts by 2027.
Use AI-powered email filters and keep yourself informed to stay ahead. For up-to-date threat information, follow CISA.gov or X’s #CyberSec threads. The best defense is constant learning.
Conclusion
Fake emails are a digital minefield, but you’re not defenseless. By understanding their tactics, spotting red flags, and adopting smart habits, you can outsmart scammers in 2026. Pause before you click, verify every sender, and keep your tools updated. If you manage newsletters or campaigns, explore the best email marketing services that prioritize security and deliverability, ensuring your messages reach audiences safely. Test your skills with a phishing quiz, share this guide with friends, and report fakes to stay one step ahead. Your inbox is your fortress, keep it secure!
FAQs
1. What is a fake email, and how does it differ from spam?
2. How can I tell if an email is fake or legitimate?
3. What are the most common types of fake emails in 2026?
4. What happens if I click on a fake email link or attachment?
5. How can I protect myself from fake emails in 2026?

Let's Start Your Project
Get free consultation for your digital product idea to turn it into reality!
Get StartedRelated Blog & Articles
Netizens
May 29, 2024
Strikethrough Google Docs: A Guide for Editors and Notetakers
Strikethrough text is a formatting option that draws a line through selected text. It's commonly used

Netizens
September 11, 2024
1and1 Webmail: Your Email Solution
1and1 webmail is a popular email service offered by 1&1 IONOS, a leading web hosting provider.

Netizens
June 11, 2024
How to Cite ChatGPT: A Complete Guide
ChatGPT, the wonder kid of AI language models, has become a go-to tool for brainstorming, content




